Scan WordPress Database For Malware – Have you sanitized your website after a malware attack but still see erratic behavior on the interface? Then it is time for you to manually scan the WordPress database for malware. When the database gets affected, the website will continue to show inconsistencies even after you have cleaned up the code. Identifying and removing malicious elements from the database, therefore, becomes necessary. Most new users like those who convert HTML CSS to WordPress or migrate from other formats are not aware of such techniques. This tutorial will be helpful to such website owners as well as other people with limited technical knowledge. The process will help you protect your interface by spotting hazardous items and removing them.
1. Understand The Threats – Scan WordPress Database For Malware
Scan WordPress Database For Malware – It will be pertinent to know what kind of threats you need to look out for before beginning the procedure. There are two main types of infections that you must be aware of. Let’s discuss them in detail.
i. Exploitable PHP Functions
The most common trick used by hackers is to exploit PHP functions and commands to infect an interface. These functions are not inherently flawed but are easily manipulated by unethical users. This makes it necessary to remove them from a database. You must spot the following functions:
a. base64_decode: There is hardly any hidden code in WordPress as it is an open source platform. The primary use of this function is to decipher base64-encrypted information. The presence of this function indicates suspicious activity aimed at hiding harmful code.
b. gzinflate: this is another PHP function used for decrypting enciphered data. It must be removed for the same reason explained in the above point.
c. error_reporting(0): code errors are stopped from logging or displaying if zero value is defined in this function. The presence of this function is usually proof of an unauthorized entity testing code permutations and hiding the error reports.
d. shell_exec: in the Unix OS, shells are used for processing commands. This function allows hackers to execute commands at the server level. One of the most attractive weapons for unscrupulous elements as it enables them to hijack the server.
e. eval: this is a harmful language construct which tries to process any string as a valid PHP program. Ethical users generally refrain from using this construct and its presence is a sure sign of infection.
The functions might be present in the following formats:
- “base64_decode( ”
- “base64_decode (”
- “gzinflate(”
- “gzinflate (”
- “error_reporting(0)”
- “error_reporting (0)
- “shell_exec(”
- “shell_exec (”
- “eval(”
- “eval (”
ii. Unknown Links Or iframes
Redirect links and harmful iframes are other tools which are used by rogue coders to corrupt websites. We will discuss later how you can recognize these items in your database.
2. Create A Backup – Scan WordPress Database For Malware
Before starting any kind of technical procedure, it is always sensible to create a backup of the database. You must make a copy of all the important files of your interface. This will help in restoring the website in case the process is unsuccessful.
3. Export The WordPress Database – Scan WordPress Database For Malware
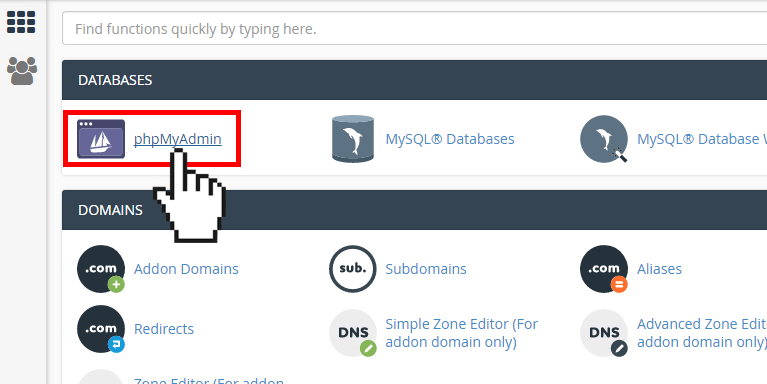
In order to manually scan WordPress database, you need to access it in a readable format. The best way is to get it in a text file which can be scanned easily for bad elements. The database can be exported as text to your system. This can be done through the cPanel of your web hosting account. Log in to the cPanel through your username and password. Locate phpMyAdmin in the “Databases” section. Click its icon to open it.
In the list on the left-hand side, you will find the database of your interface. Select it and press the “Export” button located among various options at the top of the screen.
This will open the screen shown in the following image:
Select the radio button against the “Quick” option in the “Export method” section. Choose “SQL” from the dropdown menu in “Format”. Hit the “Go” tab and the database will be downloaded to your system.
4. Search For Hazardous PHP Functions
We will now look for harmful PHP functions in the database. Open the SQL file in a text editor. Press “Ctrl + F” to initiate the search function. Now go back to the list of potentially exploitable PHP functions given in the second step. Copy a function and then paste it in the search bar of your text editor. Repeat the process to see whether any hazardous elements are present in the database or not. Once you have checked for all types of PHP functions move to the next step.
5. Use cURL To Spot Dangerous iframes And Links
It is now time to detect the presence of dangerous redirects and iframes in your interface’s code. The best way to spot these bad items on your interface is by using cURL. A handy tool that can be helpful in this purpose is Online Curl. Visit the website of this service and on the homepage, you will find a box to enter a URL. You only have to enter the complete URL of your interface and press the “Start Your Curl” button. The tool will generate the source code of your website. Using the same search technique explained in the previous step, you can spot anomalies in the code. Look for HTML sections that are inconsistent with the nature of your interface. List down all bad HTML along with unsafe links and iframes.
6. Sanitize The Database
Once you have identified all the malicious items, it is now time to remove them. Go back to the phpMyAdmin section of your cPanel and locate your database. Select it and then click the “Search” tab.
A new screen will open where you will see a search field named “Words or values to search for”. Enter the string or link you want to detect in the database. In the “Find” section, check the radio button against the “at least one of the words” option. Scroll down and in the “Inside Tables” section, select all the tables. Hit the “Go” tab.
In the search results, you can see how many instances of the given search term were found or not. You can select the “Browse” option to view the item or select “Delete” to remove it from the database.
Conclusion
This simple process to manually scan WordPress database will help you identify all the hazardous elements. In case, you do not feel confident enough to execute the procedure, contact experts to do the job.
Author Bio:
I am Jacob Graves Working as a WordPress Developer on a WordPress website development company Hirewpgeeks Ltd. I like to share WordPress, SMO, and SEO related tutorials. You can Follow me on Twitter.